- 1. Use a password manager
- 2. Use two-factor or multi-factor authentication
- 3. DON’T have authentication codes texted to you
- 4. Use a VPN
- 5. Use burner email address
- 6. Ask data brokers to delete information they hold on you
- 7. Lock down or delete social media accounts
- 8. Don’t share too much online
- 9. Opt out of sharing data
Since Peter Steiner’s now-famous and frequently referenced animation, “On the Internet, Nobody Knows You’re a Dog,” first appeared in The New Yorker in 1993, a lot has changed.
But these days, quite a few individuals on the Internet probably know for sure if you’re a canine or not. They likely also know your name, how you appear, where you reside, where you work, when you were born, the name of the first school you attended, and possibly even your mother’s maiden name.
Identity theft accounted for 68% of cases reported to the National theft Database in 2022, and the majority of these cases (86%) were the result of online exchanges, according to Cifas, a cross-industry UK fraud protection program. If that sounds terrifying, it probably should be.
If someone is able to put together enough information about you, they can establish bank accounts in your name and use them to apply for loans, launder money, and other things. After that, you’ll be pursued for repayment of those debts, and the authorities might suspect you of being involved in money laundering. Sorting this out and demonstrating that it wasn’t you can be time-consuming, stressful, and even cost you your employment. Protecting your name should be your top concern because identity theft can destroy your life.
And other people besides scammers might be interested in your details. Being lax about privacy and security online means you could inadvertently arm just about anyone with information about your interests and whereabouts, from that person who used to terrorise you at school who now keeps trying to add you on Facebook, to a vindictive ex-partner, or that awful fleeting acquaintance who keeps trying to get you to endorse them on LinkedIn (if you’re reading this, please leave me alone).
Fortunately, you have access to a variety of tools as well as best practices and preventative measures that can help you better secure your online identification. The major ones are listed here for you to be aware of and use.
1. Use a password manager
Guessing your passwords and logging into accounts that hold that information is one method for people to access your confidential information.
It is tedious and impracticable to keep distinct passwords for each and every account you use.
For everything that needs a password, you could create secure, one-of-a-kind passwords. You could even write down these passwords on paper or in a notebook and store them safely. That clearly isn’t practical for situations where you’re on the go.
Theoretically, you could bring that notepad with you, but if you do, you’ll need to reset all of the credentials and start over if you misplace your notebook. If it’s been taken, you’ve just provided the thief access to a genuine informational treasure trove.
Another option is to enroll into other apps and services using a third-party service, like Facebook or Google. This is obviously more handy, but it also gives Facebook, Google, or whoever else a better understanding of your browsing and spending patterns.
Use of a password manager, an application that saves and encrypts login information for every service you use behind a single, powerful master password, is a more sensible choice.
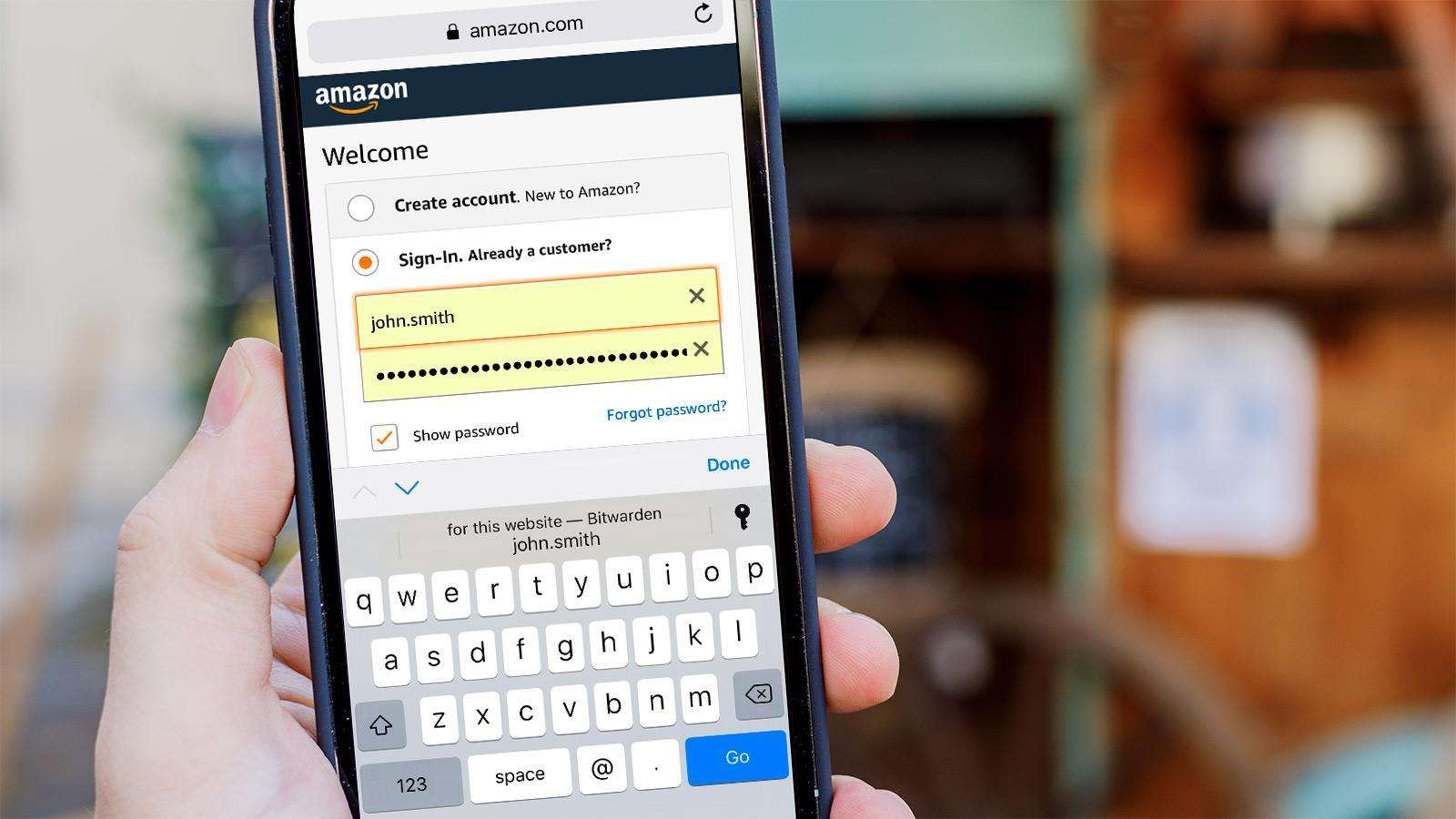
The best password organizers enable biometric logins, which let you use fingerprint readers and front-facing webcams on your phone, laptop, or PC to verify that you are the one logging in and not someone else.
Multi-factor authentication is another feature that a good password organizer will support by default. This means that after you enter your master password properly, you’ll also need to enter a second number that was safely sent to you through another app. In relation to that…
2. Use two-factor or multi-factor authentication
Two-factor authentication, also known as “2FA” or “two-step verification,” is a straightforward but efficient method to add an additional degree of security to any account you frequently sign in to.
With two-factor authentication enabled, you will receive a four- or six-digit number to input after providing your password, which serves as the first component of verification.
You can’t enter if you don’t have access to the second pass. Therefore, even if someone successfully guesses your password, they will still be unable to access your account.
Authy, Duo Mobile, Google Authenticator, or Microsoft Authenticator are some examples of authenticator apps that can send you authentication credentials. This is the finest method. Some password organizers, including Dashlane and 1Password, have built-in authenticators of their own.
Read also : Creative Zen Air Review 2023
You might also think about purchasing a protection pass. These hardware components must be connected to a USB port on your notebook or touched on your phone to identify using NFC. Similar to your house keys, you must be cautious not to misplace them, and there aren’t many internet services that support them.
Options for security keys include Thetis’s FIDO2, CryptoTrust’s OnlyKey, and Yubico’s YubiKey 5C.
3. DON’T have authentication codes texted to you
Although texting you authentication codes from businesses is a fantastic idea in principle, it’s not a good idea in reality.
The reason for this is straightforward: SMS text messages can be intercepted without the use of expensive tools or sophisticated technological expertise. Your online bank account, financial assets, or whatever else you’re attempting to log in to could all be easily accessed once someone has your login pass.
If a website offers two-factor authentication, see if you can use an authenticator software rather than receiving codes via email or SMS.
It might also be possible to request to receive login credentials via email. That is a safer choice because your email service should encrypt communications in transit by default. You run the danger of having your email account hacked.
Because of this, it’s a good idea to routinely remove any verification emails that are sent to your account.
4. Use a VPN
A virtual private network or VPN, is a good way to protect your online activity because it protects all of your network data, making it impossible for anyone to keep track of your online activities.
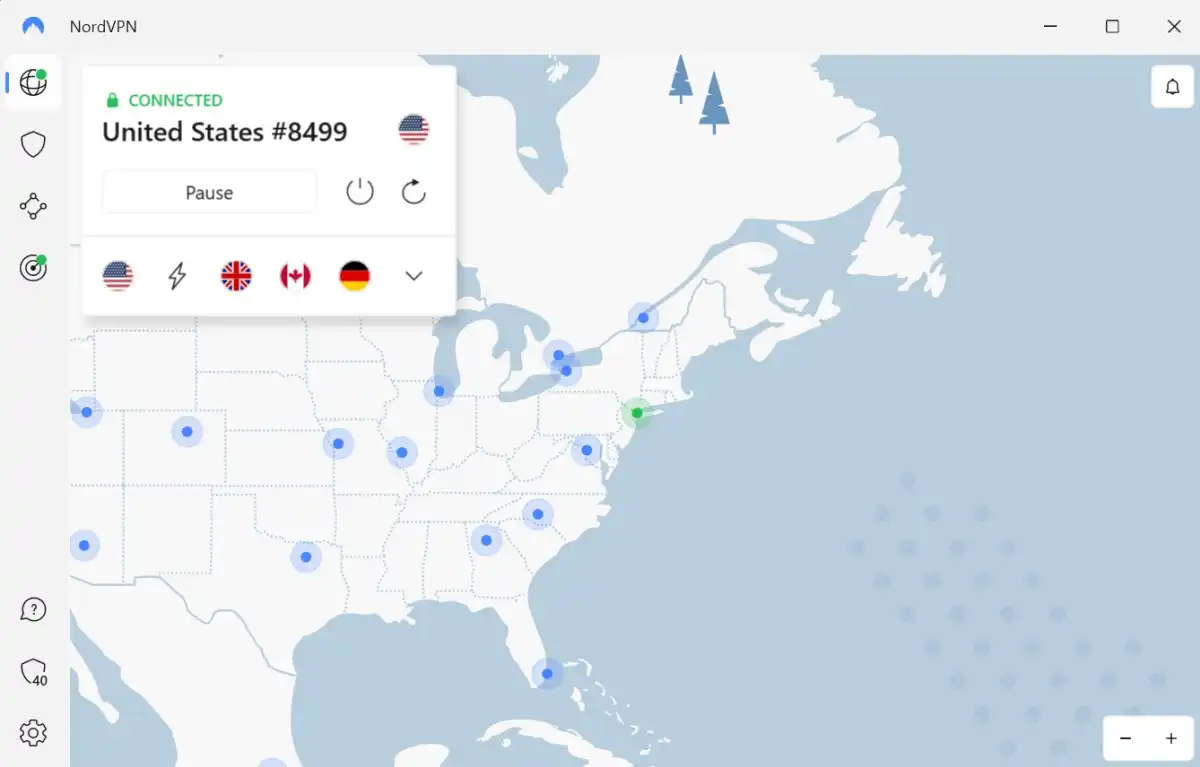
Well, almost anyone – the VPN provider itself is the only entity that could know which websites and services you access and register into.
This is why it’s critical to ask whether a VPN service strictly adheres to the “no connection logs” policy and, more significantly, whether this policy has been independently verified.
In our most current round of testing, NordVPN, CyberGhost, and PureVPN all passed this test; for a detailed breakdown, see our round-up of the top VPN services.
5. Use burner email address
Even though signing up for newsletters can be a fantastic way to learn about sales and receive discount coupons, it might be a good idea to use a separate email account for this purpose rather than your primary one.
When marketing firms exchange user information with data brokers, which can result in you receiving numerous marketing emails for items you never even signed up for in the first place or aren’t even interested in, it’s not great, even though 2-for-1 deals and inexpensive pizza are fantastic.
While that by itself does not pose a security risk, it may make it more difficult for you to recognize scam emails and other phishing efforts, which frequently masquerade as trustworthy commercial emails. Who desires junk letters, too? No-one.
If all marketing traffic is directed to a single email address, your mail account is left with letters you might want to peruse.
6. Ask data brokers to delete information they hold on you
Data aggregators like Acxiom, Equifax, Experian, and TransUnion profit from the sale of your personal information to marketing firms.

As mentioned above, businesses selling your data to third parties may obtain information about you. Other sources of information about you include analyses of your online browsing and purchasing patterns.
The General Data Protection Regulation (GDPR) of the EU is still in effect even though the UK has departed the EU.
Under Article 21 of the GDPR, you can order companies to stop processing any personal data they hold on you for the purposes of marketing, and under Article 15, you have the right to make a SAR (subject access request), where a company must share all and any personal data they hold about you, for free.
Your rights in the United States presently vary depending on the state you live in, but you may still be effective in contacting a business or organization with a SAR, or SRR (subject rights request), as they are also known. The U.S.-based non-profit Privacy Rights Clearinghouse keeps a roster of data brokers, along with information about the jurisdictions in which they operate and whether or not they provide an opt-out option.
According to the Australian Privacy Act, you have the right to view the information that a business has on you and ask them to correct any information that is inaccurate, delete it, or de-identify it if it is no longer needed.
In order to make any kind of access request, you will need to provide some basic information – such as your name, home address, phone number email address – and possibly some supplementary information, such as your account name/user ID, so that a company can correctly identify you and process your request.
If you don’t have the time to do it yourself, you can also hire others to call data brokers on your account. Companies that provide this service include DeleteMe, Incogni, OneRep, OptOutUK, and PrivacyBee.
However, responses to queries made by third parties like these on behalf of specific people may not be provided by data brokers. It’s possible that a business can only tell you who has information about you; in that case, it would be up to you to get in touch with that business and ask them to remove any information they may have.
7. Lock down or delete social media accounts

There is information you’ve shared online on a platform that you haven’t updated or kept in a while, so there’s a possibility that someone could access your profile, whether or not it’s damaging to your image or personal credibility. Any outdated accounts that are still connected to live email addresses should be deleted.
In other words, if you aren’t using Facebook, Twitter, Instagram, or any other network anymore, think about deleting it or, at the very least, lock down the private options to limit who can access that data. So, even though you continue to be active on those platforms, it is much less likely that someone will attempt to mimic you using them.
8. Don’t share too much online
Stewart Lee, a renowned comedian who once notably compared Twitter to “the Stasi for the Angry Birds generation,” is not active on any social media platforms.
Although you might not want to use the same strategy as Mr. Lee on social media, his primary point about disclosing one’s whereabouts and routines on an open online platform like Twitter is something to remember.
Posting a photo of you in front of the house you’ve recently moved into, then later complaining that your landlord still hasn’t fixed that downstairs window, and then announcing to the world that you’re about to go on holiday for a couple of weeks, could all add up to you coming back home to a nasty surprise.
9. Opt out of sharing data
Read the terms and conditions of everything you join up for, and whenever possible, choose not to share your data. It’s easy to ignore the text on the installation or greeting displays by clicking or tapping through them. You frequently have the option to restrict the amount of data you share with that business, but you must carefully study the displays to determine whether you should check a box or select the Decline button.
Additionally, be careful with what you disclose online and consider how someone viewing your page might connect the connections. To better secure yourself and your online activity, use some form of multi-factor authentication, but avoid having codes sent to you via SMS if at all possible. You should also think about using a password organizer and a VPN.


